QUANTUM

Foreword
The RSA cryptographic platform is now 40 years old. Although it has functioned well in securing Internet and digital communications, the day is counted due to Moore's unremitting legal progress and the emergence of Quantum computing. Significant efforts and resources are employed by hackers to break the RSA and in the form of encryption. With Quantum computing, every quantum bit (called a qubit) can both be zero and one at the same time. This difference means that Quantum computers can store more data, and do more calculations per second, making it perfect for decoding applications. The rise of Quantum computing makes RSA cracking and other forms of encryption feasible in the near future. The classical computer uses binary bits, which have a value of zero and one.
With this Quantum computing technology on the cusp of a breakthrough makes Quantum ready to solve existing encryption methods. Once RSA is cracked, mission critical applications such as https, credit and debit processing, and government systems face the risk of direct compromise. The chaos of such a hack would really disrupt the social and economic framework of everyday life.
Quantum1Net Mission
The Quantum1Net mission is to create enabling and enabling technologies. We have designed a very safe product so you do not have to worry now or in the future about the security of your data. We introduce an unparalleled level of technical innovation, combined with user-connected system design to provide security, ease of use, and ultimate peace of mind.
Quantum Computing
Quantum Computing makes it possible for Quantum bits, called qubits to store large amounts of information at the same time need less energy to do so. The result is much better computer capable of running a much more complicated calculation, and much faster than an ordinary computer
Ordinary computers work by storing data in a series of bits, holding either 0 or 1. String bit lengths store information, but at one time bits can only have one value or other value, so only one calculation. done at one time. Quantum computing works differently. It is based on the unique behavior of subatomic particles to be able to exist in more than one country at the same time.
End of RSA Encryption
Electronic communications have been secured by a method known as RSA, named for three researchers who developed this method: Ron Rivest, Adi Shamir, and Leonard Adleman. It takes a large amount of computing power to produce and then calculates these numbers, something that is not possible with ordinary computing techniques. The difficulty in doing so is illustrated in a 2009 study. Researchers found that 768 bits (232 digits) spent hundreds of machines and almost two years for cracking, while RSA 1024 bit keys take a thousand times longer, and that is the smallest type of RSA key currently used. The reliability of RSA depends on traditional computing boundaries while technology is rapidly developing and the emergence of quantum computing is imminent requires a new encryption strategy. Much less resources and time needed to break even the strongest RSA keys with quantum computing. Quantum computing empowers first credential threats against RSA encryption from the start.
Quantum Computing and Code Solving
Before Quantum computers will have a positive effect on the technology industry, their expertise also brings up issues of security issues. RSA depends on the complexity of a large amount of factorization to store encrypted data. Because of its architecture, quantum computing becomes a straightforward solution to this problem. Because qubits have the advantage of having a state at the same time called superposition of circumstances, enabling many calculations, Quantum computers become logical code-breaking mechanisms. Work is underway, and NIST expects a quantum computer capable of breaking RSA2048 in a matter of hours by 2030 to be purchased for about a billion dollars.
Quantum Encryption Key
The Quantum Key Encryption Generator is at the core of the Quantum1Net encryption strategy. To review, generate a multi-digit random number from which the mathematical property is derived in case of RSA primary factorization. However there is one major problem, random generators are used only pseudo-random (commonly called PRNGs), so RSA keys are pseudo random. Tests show that PRNG shows repetitive behavior patterns when selecting random numbers. This pattern means that with sufficient results, predictions can be made for the selection of the number in the future. That way, PRNG is not really random.
Quantum1Net instead relies on Quantum Encryption Key Generator (QEKG). Due to the nature of the quantum computer itself, tests have shown that in large samples the number chosen does not follow the pattern so that no predictive algorithm can be derived.
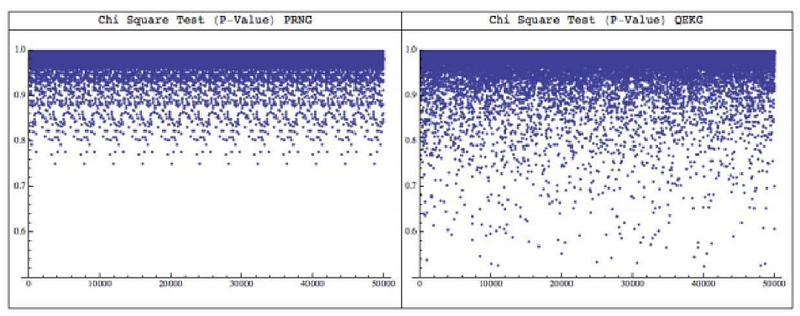
This graph shows the results of PRNG and QEKG tests on a sample size of 20,000 bits 50,000 times. By using PRNG, after 50,000 tests, it is seen visually that the data is predictive even after 10,000 or more first experiments. With QEKG however it is not the case. Look at the bottom of the graph where the dots are more dispersed. Unlike PRNG graphs, on the QEKG chart there is no clear pattern to their location.
NSA and iQuantum Computas
Quantum Computing has gained the attention of the U.S. spy agency. top. Documents leaked by former NSA contractor Ed Snowden in 2014, indicate that the agency is funding a $ 80 million project aimed at building a highly useful quantum computer cryptologically. NSA officials hope that such a machine will allow them to dramatically improve digital spy efforts. From these documents, it appears that the NSA is not anywhere near quantum computers to work on, but still follows some of the world's leading quantum computing labs.
Quantum1Net prototype
The Quantum1Net Generator random number generator prototype, which has been developed since 2014 is based on a qubit optical device that uses four photon detectors and a Time-to-Digital converter to produce a perfect set of random numbers. with time stamp The quantum device consists of an entangled photon source, and a linear optical element, which determines the quantum system to the desired state. Two configurations have been developed to produce each set of 4 and 6 elements.
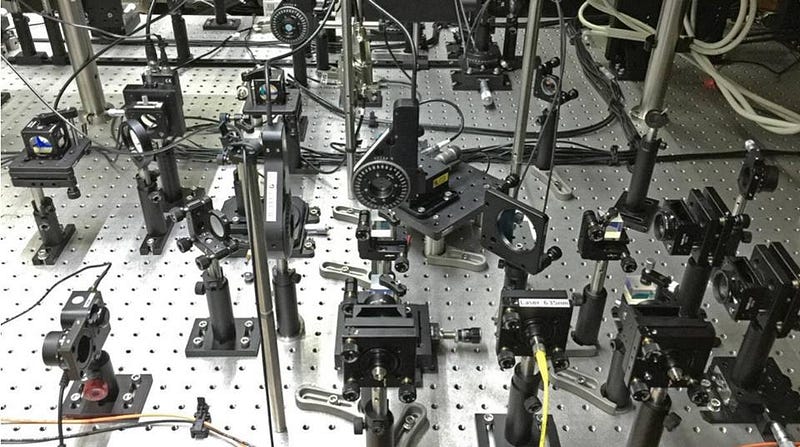
The output of TDC or time to digital is a temporary queue, from which a set of random numbers or unique encryption keys can be requested, creating real time, on demand encryption and decryption systems.
Quantum Tokens
Timeline ICO
Sales Token # 1: silver token
Ethereum based
February 2018
Convert to Gold Token with 20% off
Sales limit of 15 million
Sales Token # 2: Gold Token
July 2018
Bitcoin-based, including QEK
Silver Token investors get priority
Sales limit of 18 million
Sales Token # 3: Gold Token
January 2019
Bitcoin based, QE activated
Silver Silver Investors converting on July 2018 sales may participate at a 5%
Sales Limit 200 million
For more details please visit our web site:
Website: https: //quantum1net.com/
Whitepaper: https: //quantum1net.com/Q1N%20white%20paper.pdf
Facebook: https: //web.facebook.com/quantum1net
Twitter: https: //twitter.com/quantum1net
Telegram: https: //t.me/Quantum1Net
Author: wily27
bitcointalk profile : https://bitcointalk.org/index.php?action=profile;u=1816724

Komentar
Posting Komentar